About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 99 results for "Phesi Project" clear search
PaCE Austria Pilot Model
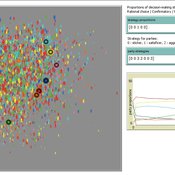
Ruth Meyer | Published Tuesday, June 30, 2020The objective of building a social simulation in the Populism and Civic Engagement (PaCE) project is to study the phenomenon of populism by mapping individual level political behaviour and explain the influence of agents on, and their interdependence with the respective political parties. Voters, political parties and – to some extent – the media can be viewed as forming a complex adaptive system, in which parties compete for citizens’ votes, voters decide on which party to vote for based on their respective positions with regard to particular issues, and the media may influence the salience of issues in the public debate.
This is the first version of a model exploring voting behaviour in Austria. It focusses on modelling the interaction of voters and parties in a political landscape; the effects of the media are not yet represented. Austria was chosen as a case study because it has an established populist party (the “Freedom Party” FPO), which has even been part of the government over the years.
Memetic Exploration of Demand
rolanmd | Published Monday, August 09, 2010 | Last modified Saturday, April 27, 2013In this presentation, we use the concept of meme to explore evolution of demand.
Reflexivity in a diffusion of innovations model
Carlos Cordoba César García-Díaz | Published Thursday, May 07, 2020In this agent-based model, agents decide to adopt a new product according to a utility function that depends on two kinds of social influences. First, there is a local influence exerted on an agent by her closest neighbors that have already adopted, and also by herself if she feels the product suits her personal needs. Second, there is a global influence which leads agents to adopt when they become aware of emerging trends happening in the system. For this, we endow agents with a reflexive capacity that allows them to recognize a trend, even if they can not perceive a significant change in their neighborhood.
Results reveal the appearance of slowdown periods along the adoption rate curve, in contrast with the classic stylized bell-shaped behavior. Results also show that network structure plays an important role in the effect of reflexivity: while some structures (e.g., scale-free networks) may amplify it, others (e.g., small-world structure) weaken such an effect.
Endogenous Corruption as a Cellular Automaton
Warren Vierheller | Published Wednesday, June 27, 2018The model explores how corruption may spread endogenously within a closed society by depicting the behavior within a cellular automaton context (CA) between bureaucrats and citizens. Within the model, corruption is characterized as a behavior product dependent upon an individual’s personal disposition towards honesty, rational decisionmaking processes, and neighbors’ behavior.
Peer reviewed BAMERS: Macroeconomic effect of extortion
Alejandro Platas López Alejandro Guerra-Hernández | Published Monday, March 23, 2020 | Last modified Sunday, July 26, 2020Inspired by the European project called GLODERS that thoroughly analyzed the dynamics of extortive systems, Bottom-up Adaptive Macroeconomics with Extortion (BAMERS) is a model to study the effect of extortion on macroeconomic aggregates through simulation. This methodology is adequate to cope with the scarce data associated to the hidden nature of extortion, which difficults analytical approaches. As a first approximation, a generic economy with healthy macroeconomics signals is modeled and validated, i.e., moderate inflation, as well as a reasonable unemployment rate are warranteed. Such economy is used to study the effect of extortion in such signals. It is worth mentioning that, as far as is known, there is no work that analyzes the effects of extortion on macroeconomic indicators from an agent-based perspective. Our results show that there is significant effects on some macroeconomics indicators, in particular, propensity to consume has a direct linear relationship with extortion, indicating that people become poorer, which impacts both the Gini Index and inflation. The GDP shows a marked contraction with the slightest presence of extortion in the economic system.
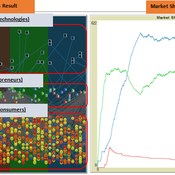
The simulation on the study of the optimal business strategy with the interaction between technologies and consumers.
sej-yoo | Published Monday, June 27, 2022 | Last modified Monday, July 04, 2022HOW IT WORKS
This model consists of three agents, and each agent type operates per business theories as below.
a. New technologies(Tech): It evolves per sustaining or disruptive technology trajectory with the constraint of project management triangle (Scope, Time, Quality, and Cost).
b. Entrepreneurs(Entre): It builds up the solution by combining Tech components per its own strategy (Exploration, Exploitation, or Ambidex).
c. Consumer(Consumer): It selects the solution per its own preference due to Diffusion of innovation theory (Innovators, Early Adopters, Early Majority, Late Majority, Laggards)
…
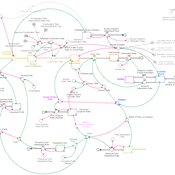
Endogenous Dynamics of Housing Market Cycles
Birnur Özbaş Onur Özgün Yaman Barlas | Published Monday, September 09, 2013 | Last modified Wednesday, January 08, 2014The purpose of this model is to analyze the dynamics of endogenously created oscillations in housing prices using a system dynamics simulation model, built from the perspective of construction companies.
The various technologies used inside a Dutch greenhouse interact in combination with an external climate, resulting in an emergent internal climate, which contributes to the final productivity of the greenhouse. This model examines how differing technology development styles affects the overall ability of a community of growers to approach the theoretical maximum yield.
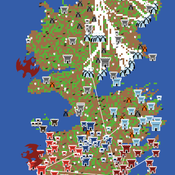
Game of Thrones model
Claudine Gravel-Miguel Sean Bergin | Published Sunday, January 03, 2021 | Last modified Sunday, January 03, 2021This model slowly evolves to become Westeros, with houses fighting for the thrones, and whitewalkers trying to kill all living things. You can download each version to see the evolution of the code, from the Wolf Sheep Predation model to the Game of Thrones model. If you are only interested in the end product, simply download the latest version.
For instructions on each step, see: https://claudinegravelmigu.wixsite.com/got-abm
Oneshot negotiation in Colored Trails
Harmen de Weerd | Published Tuesday, April 09, 2019This model allows for oneshot negotiations in the Colored Trails setting. Two allocator agents simultaneously make an offer to a responder agent, who chooses which of these offers to accept, or to reject both offers. The code allows for allocator allocator agents of different orders of theory of mind reasoning to play against one another.
Displaying 10 of 99 results for "Phesi Project" clear search