About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 168 results for "Jennifer Fewell" clear search
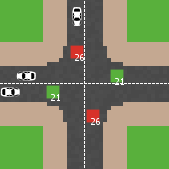
Modelling an intersection with traffic signal countdown timer
Eduard | Published Thursday, May 19, 2022Developed as a part of a project in the University of Augsburg, Institute of Geography, it simulates the traffic in an intersection or junction which uses either regular traffic lights or traffic lights with a countdown timer. The model tracks the average speed of cars before and after traffic lights as well as the throughput.
Intra-Organizational Bandwagon
Davide Secchi | Published Sunday, October 18, 2015The model simulates the process of widespread diffusion of something due to popularity (i.e., bandwagon) within an organization.
Proof of principle for a self-governing prediction and forecasting reward algorithm: Modeling consensus of a group of experts in adversarial collaboration.
Jose Osvaldo Gonzalez Hernandez Jonathan Marino Ted C. Rogers Brandon Velasco | Published Sunday, May 14, 2023Package for simulating the behavior of experts in a scientific-forecasting competition, where the outcome of experiments itself depends on expert consensus. We pay special attention to the interplay between expert bias and trust in the reward algorithm. The package allows the user to reproduce results presented in arXiv:2305.04814, as well as testing of other different scenarios.
Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats
kpadur | Published Friday, September 20, 2024Hybrid attacks coordinate the exploitation of vulnerabilities across domains to undermine trust in authorities and cause social unrest. Whilst such attacks have primarily been seen in active conflict zones, there is growing concern about the potential harm that can be caused by hybrid attacks more generally and a desire to discover how better to identify and react to them. In addressing such threats, it is important to be able to identify and understand an adversary’s behaviour. Game theory is the approach predominantly used in security and defence literature for this purpose. However, the underlying rationality assumption, the equilibrium concept of game theory, as well as the need to make simplifying assumptions can limit its use in the study of emerging threats. To study hybrid threats, we present a novel agent-based model in which, for the first time, agents use reinforcement learning to inform their decisions. This model allows us to investigate the behavioural strategies of threat agents with hybrid attack capabilities as well as their broader impact on the behaviours and opinions of other agents.
(Policy induced) Diffusion of Innovations - An integrated demand-supply Model based on Cournot Competition
Martin Rixin | Published Monday, August 29, 2011 | Last modified Saturday, April 27, 2013Objective is to simulate policy interventions in an integrated demand-supply model. The underlying demand function links both sides. Diffusion proceeds if interactions distribute awareness (Epidemic effect) and rivalry reduces the market price (Probit effect). Endogeneity is given due to the fact that consumer awareness as well as their willingness-to-pay drives supply-side rivalry. Firm´s entry and exit decisions as well as quantity and price settings are driven by Cournot competition.
Policy Formulation for Public Administration - Innovation
Bashar Ourabi | Published Tuesday, August 29, 2017 | Last modified Tuesday, August 29, 2017Innovation a byproduct of the intellectual capital, requires a new paradigm for the production constituents. Human Capital HC,Structural capital SC and relational capital RC become key for intellectual capital and consequently for innovation.
Agent-based Simulation of Time Management
Hang Xiong | Published Thursday, March 24, 2016 | Last modified Friday, March 25, 2016This model simulates how the strategy one manages time affect the well-being that he/she can obtain.
Consumer diets and values ABM
Natalie Davis Merlin Radbruch | Published Thursday, December 22, 2022 | Last modified Wednesday, March 05, 2025An agent-based model of individual consumers making choices between five possible diets: omnivore, flexitarian, pescatarian, vegetarian, or vegan. Each consumer makes decisions based on personal constraints and values, and their perceptions of how well each diet matches with those values. Consumers can also be influenced by each other’s perceptions via interaction across three social networks: household members, friends, and acquaintances.
Social Nets Emergence Model
Di Wang | Published Wednesday, March 21, 2012 | Last modified Saturday, April 27, 2013This model simulates the interactions and dynamic trust changes between people which results in social group emergence and evolution.
Homophily as a process generating social networks: insights from Social Distance Attachment model
Szymon Talaga Andrzej Nowak | Published Tuesday, September 17, 2019This is code repository for the paper “Homophily as a process generating social networks: insights from Social Distance Attachment model”.
It provides all information, code and data necessary to replicate all the simulations and analyses presented in the paper.
This document contains the overall instruction as well as description of the content of the repository.
Details regarding particular stages are documented within source files as comments.
Displaying 10 of 168 results for "Jennifer Fewell" clear search