About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 132 results #Networks clear search
Consumer diets and values ABM
Natalie Davis Merlin Radbruch | Published Thursday, December 22, 2022 | Last modified Wednesday, March 05, 2025An agent-based model of individual consumers making choices between five possible diets: omnivore, flexitarian, pescatarian, vegetarian, or vegan. Each consumer makes decisions based on personal constraints and values, and their perceptions of how well each diet matches with those values. Consumers can also be influenced by each other’s perceptions via interaction across three social networks: household members, friends, and acquaintances.
We provide a theory-grounded, socio-geographic agent-based model to present a possible explanation for human movement in the Adriatic region within the Cetina phenomenon.
Focusing on ideas of social capital theory from Piere Bordieu (1986), we implement agent mobility in an abstract geography based on cultural capital (prestige) and social capital (social position). Agents hold myopic representations of social (Schaff, 2016) and geographical networks and decide in a heuristic way on moving (and where) or staying.
The model is implemented in a fork of the Laboratory for Simulation Development (LSD), appended with GIS capabilities (Pereira et. al. 2020).
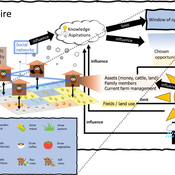
3spire: an agent-based model for exploring aspiration adaptation theory and its implications on smallholder farmers in Ethiopia
ateeuw Yue Dou Markus A Meyer Andrew Nelson | Published Sunday, February 16, 20253spire is an ABM where farming households make management decisions aimed at satisficing along the aspirational dimensions: food self-sufficiency, income, and leisure. Households decision outcomes depend on their social networks, knowledge, assets, household needs, past management, and climate/market trends
ABM Code: Locating Cultural Holes Brokers in Diffusion Dynamics across Bright Symbolic Boundaries
Diego Leal | Published Thursday, January 23, 2025The code and data in this repository are associated with the article titled: “Locating Cultural Holes Brokers in Diffusion Dynamics across Bright Symbolic Boundaries.” The NetLogo code (version 6.4.0) is designed to be a standalone piece of code although it uses the ‘nw’ and ‘matrix’ extensions that come integrated with NetLogo 6.4.0. The code was ran on a Windows 10 x 64 machine.
The impact of scientific networks, affinity bias and scientific uncertainty on the public uptake of science
Sacha Ferrari | Published Thursday, January 23, 2025Ferrari, S., Lammers, W., Wenmackers, S. (forthcoming) How the structure of scientific communities could impact the public uptake of uncertain science. Philosophy of Science.
Peer reviewed Descriptive Norm and Fraud Dynamics
Alexandra Eckert Matthias Meyer Christian Stindt | Published Tuesday, January 07, 2025The “Descriptive Norm and Fraud Dynamics” model demonstrates how fraudulent behavior can either proliferate or be contained within non-hierarchical organizations, such as peer networks, through social influence taking the form of a descriptive norm. This model expands on the fraud triangle theory, which posits that an individual must concurrently possess a financial motive, perceive an opportunity, and hold a pro-fraud attitude to engage in fraudulent activities (red agent). In the absence of any of these elements, the individual will act honestly (green agent).
The model explores variations in a descriptive norm mechanism, ranging from local distorted knowledge to global perfect knowledge. In the case of local distorted knowledge, agents primarily rely on information from their first-degree colleagues. This knowledge is often distorted because agents are slow to update their empirical expectations, which are only partially revised after one-to-one interactions. On the other end of the spectrum, local perfect knowledge is achieved by incorporating a secondary source of information into the agents’ decision-making process. Here, accurate information provided by an observer is used to update empirical expectations.
The model shows that the same variation of the descriptive norm mechanism could lead to varying aggregate fraud levels across different fraud categories. Two empirically measured norm sensitivity distributions associated with different fraud categories can be selected into the model to see the different aggregate outcomes.
BarterNet is a platform for modeling early barter networks with the aim of learning how supply and demand for a good determine if traders will learn to use that good as a form of money. Traders use a good as money when they offer to trade for it even if they can’t consume it, but believe that they can subsequently trade it for a good they can consume in the near future.
Peer reviewed Credit and debt market of low-income families
Márton Gosztonyi | Published Tuesday, December 12, 2023 | Last modified Friday, January 19, 2024The purpose of the Credit and debt market of low-income families model is to help the user examine how the financial market of low-income families works.
The model is calibrated based on real-time data which was collected in a small disadvantaged village in Hungary it contains 159 households’ social network and attributes data.
The simulation models the households’ money liquidity, expenses and revenue structures as well as the formal and informal loan institutions based on their network connections. The model forms an intertwined system integrated in the families’ local socioeconomic context through which families handle financial crises and overcome their livelihood challenges from one month to another.
The simulation-based on the abstract model of low-income families’ financial survival system at the bottom of the pyramid, which was described in following the papers:
…
Peer reviewed MADTOR: Model for Assessing Drug Trafficking Organizations Resilience
Deborah Manzi | Published Friday, February 23, 2024Criminal organizations operate in complex changing environments. Being flexible and dynamic allows criminal networks not only to exploit new illicit opportunities but also to react to law enforcement attempts at disruption, enhancing the persistence of these networks over time. Most studies investigating network disruption have examined organizational structures before and after the arrests of some actors but have disregarded groups’ adaptation strategies.
MADTOR simulates drug trafficking and dealing activities by organized criminal groups and their reactions to law enforcement attempts at disruption. The simulation relied on information retrieved from a detailed court order against a large-scale Italian drug trafficking organization (DTO) and from the literature.
The results showed that the higher the proportion of members arrested, the greater the challenges for DTOs, with higher rates of disrupted organizations and long-term consequences for surviving DTOs. Second, targeting members performing specific tasks had different impacts on DTO resilience: targeting traffickers resulted in the highest rates of DTO disruption, while targeting actors in charge of more redundant tasks (e.g., retailers) had smaller but significant impacts. Third, the model examined the resistance and resilience of DTOs adopting different strategies in the security/efficiency trade-off. Efficient DTOs were more resilient, outperforming secure DTOs in terms of reactions to a single, equal attempt at disruption. Conversely, secure DTOs were more resistant, displaying higher survival rates than efficient DTOs when considering the differentiated frequency and effectiveness of law enforcement interventions on DTOs having different focuses in the security/efficiency trade-off.
Overall, the model demonstrated that law enforcement interventions are often critical events for DTOs, with high rates of both first intention (i.e., DTOs directly disrupted by the intervention) and second intention (i.e., DTOs terminating their activities due to the unsustainability of the intervention’s short-term consequences) culminating in dismantlement. However, surviving DTOs always displayed a high level of resilience, with effective strategies in place to react to threatening events and to continue drug trafficking and dealing.
Peer reviewed Visibility of archaeological social networks
Claudine Gravel-Miguel | Published Sunday, November 26, 2023The purpose of this model is to explore the impact of combining archaeological palimpsests with different methods of cultural transmission on the visibility of prehistoric social networks. Up until recently, Paleolithic archaeologists have relied on stylistic similarities of artifacts to reconstruct social networks. However, this method - which is successfully applied to more recent ceramic assemblages - may not be applicable to Paleolithic assemblages, as several of those consist of palimpsests of occupations. Therefore, this model was created to study how palimpsests of occupation affect our social network reconstructions.
The model simplifies inter-groups interactions between populations who share cultural traits as they produce artifacts. It creates a proxy archaeological record of artifacts with stylistic traits that can then be used to reconstruct interactions. One can thus use this model to compare the networks reconstructed through stylistic similarities with direct contact.
Displaying 10 of 132 results #Networks clear search