About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 132 results networks clear search
Waste separation in small-world networks
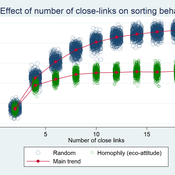
František Kalvas Michaela Kudrnáčová | Published Monday, September 30, 2019The model answers the question how homophily and number of close-links in small-world network influences behavior of consumats. The results show that the more close-links the more probable the consumat follows the major behavior, but homophilly blocks the major behavior and supports survival of the minor behavior.
Homophily as a process generating social networks: insights from Social Distance Attachment model
Szymon Talaga Andrzej Nowak | Published Tuesday, September 17, 2019This is code repository for the paper “Homophily as a process generating social networks: insights from Social Distance Attachment model”.
It provides all information, code and data necessary to replicate all the simulations and analyses presented in the paper.
This document contains the overall instruction as well as description of the content of the repository.
Details regarding particular stages are documented within source files as comments.
NarcoLogic
Nicholas Magliocca | Published Thursday, August 29, 2019Investigate spatial adaptive behaviors of narco-trafficking networks in response to various counterdrug interdiction strategies within the cocaine transit zone of Central America and associated maritime areas. Through the novel application of the ‘complex adaptive systems’ paradigm, we implement a potentially transformative coupled agent-based and interdiction optimization modeling approach to compellingly demonstrate: (a) how current efforts to disrupt narco-trafficking networks are in fact making them more widespread, resilient, and economically powerful; (b) the potential for alternative interdiction approaches to weaken and contain traffickers.
Relational integration in schools through seating assignments
Marta Rado Károly Takács | Published Thursday, July 18, 2019We model interpersonal dynamics and study behavior in the classroom in the hypothetical case of a single teacher who defines students’ seating arrangements. The model incorporates the mechanisms of peer influence on study behavior, on attitude formation, and homophilous selection in order to depict the interrelated dynamics of networks, behavior, and attitudes. We compare various seating arrangement scenarios and observe how GPA distribution and level of prejudice changes over time.
MERCURY extension: population
Tom Brughmans | Published Thursday, May 23, 2019This model is an extended version of the original MERCURY model (https://www.comses.net/codebases/4347/releases/1.1.0/ ) . It allows for experiments to be performed in which empirically informed population sizes of sites are included, that allow for the scaling of the number of tableware traders with the population of settlements, and for hypothesised production centres of four tablewares to be used in experiments.
Experiments performed with this population extension and substantive interpretations derived from them are published in:
Hanson, J.W. & T. Brughmans. In press. Settlement scale and economic networks in the Roman Empire, in T. Brughmans & A.I. Wilson (ed.) Simulating Roman Economies. Theories, Methods and Computational Models. Oxford: Oxford University Press.
…
Nudging agents in social networks for collective action
Marco Janssen | Published Sunday, August 14, 2011 | Last modified Sunday, March 17, 2019Agents are linked in a social-network and make decisions on which of 2 types of behavior to adopt. We explore consequences of different information feedback and providing targeted feedback to individuals.
CONSERVAT
Pieter Van Oel | Published Monday, April 13, 2015The CONSERVAT model evaluates the effect of social influence among farmers in the Lake Naivasha basin (Kenya) on the spatiotemporal diffusion pattern of soil conservation effort levels and the resulting reduction in lake sedimentation.
LaMEStModel
Ruth Meyer | Published Friday, October 12, 2018The Labour Markets and Ethnic Segmentation (LaMESt) Model is a model of a simplified labour market, where only jobs of the lowest skill level are considered. Immigrants of two different ethnicities (“Latino”, “Asian”) compete with a majority (“White”) and minority (“Black”) native population for these jobs. The model’s purpose is to investigate the effect of ethnically homogeneous social networks on the emergence of ethnic segmentation in such a labour market. It is inspired by Waldinger & Lichter’s study of immigration and the social organisation of labour in 1990’s Los Angeles.
Network structures tutorial
Tom Brughmans | Published Sunday, September 30, 2018 | Last modified Tuesday, October 02, 2018A draft model with some useful code for creating different network structures using the Netlogo NW extension. This model is used for the following tutorial:
Brughmans, T. (2018). Network structures and assembling code in Netlogo, Tutorial, https://archaeologicalnetworks.wordpress.com/resources/#structures .
Importing a Roman transport network
Tom Brughmans | Published Sunday, September 30, 2018A draft model teaching how a Roman transport model can be imported into Netlogo, and the issues confronted when importing and reusing open access Roman datasets. This model is used for the tutorial:
Brughmans, T. (2018). Importing a Roman Transport network with Netlogo, Tutorial, https://archaeologicalnetworks.wordpress.com/resources/#transport .
Displaying 10 of 132 results networks clear search