About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 323 results for "John Nay" clear search
Bicycle encounter model
Gudrun Wallentin | Published Saturday, October 29, 2016 | Last modified Friday, March 29, 2019This Bicycle encounter model builds on the Salzburg Bicycle model (Wallentin & Loidl, 2015). It simulates cyclist flows and encounters, which are locations of potential accidents between cyclists.
Peer reviewed General Housing Model
J M Applegate | Published Thursday, May 07, 2020The General Housing Model demonstrates a basic housing market with bank lending, renters, owners and landlords. This model was developed as a base to which students contributed additional functions during Arizona State University’s 2020 Winter School: Agent-Based Modeling of Social-Ecological Systems.
Soy2Grow-ABM-V1
Siavash Farahbakhsh | Published Monday, January 20, 2025The Soy2Grow ABM aims to simulate the adoption of soybean production in Flanders, Belgium. The model primarily considers two types of agents as farmers: 1) arable and 2) dairy farmers. Each farmer, based on its type, assesses the feasibility of adopting soybean cultivation. The feasibility assessment depends on many interrelated factors, including price, production costs, yield, disease, drought (i.e., environmental stress), social pressure, group formations, learning and skills, risk-taking, subsidies, target profit margins, tolerance to bad experiences, etc. Moreover, after adopting soybean production, agents will reassess their performance. If their performance is unsatisfactory, an agent may opt out of soy production. Therefore, one of the main outcomes to look for in the model is the number of adopters over time.
The main agents are farmers. Generally, factors influencing farmers’ decision-making are divided into seven main areas: 1) external environmental factors, 2) cooperation and learning (with slight differences depending on whether they are arable or dairy farmers), 3) crop-specific factors, 4) economics, 5) support frameworks, 6) behavioral factors, and 7) the role of mobile toasters (applicable only to dairy farmers).
Moreover, factors not only influence decision-making but also interact with each other. Specifically, external environmental factors (i.e., stress) will result in lower yield and quality (protein content). The reducing effect, identified during participatory workshops, can reach 50 %. Skills can grow and improve yield; however, their growth has a limit and follows different learning curves depending on how individualistic a farmer is. During participatory workshops, it was identified that, contrary to cooperative farmers, individualistic farmers may learn faster and reach their limits more quickly. Furthermore, subsidies directly affect revenues and profit margins; however, their impact may disappear when they are removed. In the case of dairy farmers, mobile toasters play an important role, adding toasting and processing costs to those producing soy for their animal feed consumption.
Last but not least, behavioral factors directly influence the final adoption decision. For example, high risk-taking farmers may adopt faster, whereas more conservative farmers may wait for their neighbors to adopt first. Farmers may evaluate their success based on their own targets and may also consider other crops rather than soy.
How does knowledge infrastructure mobilization influence the safe operating space of regulated exploited ecosystems?
Jean-Denis Mathias | Published Tuesday, July 17, 2018Decision-makers often have to act before critical times to avoid the collapse of ecosystems using knowledge \textcolor{red}{that can be incomplete or biased}. Adaptive management may help managers tackle such issues. However, because the knowledge infrastructure required for adaptive management may be mobilized in several ways, we study the quality and the quantity of knowledge provided by this knowledge infrastructure. In order to analyze the influence of mobilized knowledge, we study how the following typology of knowledge and its use may impact the safe operating space of exploited ecosystems: 1) knowledge of the past based on a time series distorted by measurement errors; 2) knowledge of the current systems’ dynamics based on the representativeness of the decision-makers’ mental models of the exploited ecosystem; 3) knowledge of future events based on decision-makers’ likelihood estimates of extreme events based on modeling infrastructure (models and experts to interpret them) they have at their disposal. We consider different adaptive management strategies of a general regulated exploited ecosystem model and we characterize the robustness of these strategies to biased knowledge. Our results show that even with significant mobilized knowledge and optimal strategies, imperfect knowledge may still shrink the safe operating space of the system leading to the collapse of the system. However, and perhaps more interestingly, we also show that in some cases imperfect knowledge may unexpectedly increase the safe operating space by suggesting cautious strategies.
The code enables to calculate the safe operating spaces of different managers in the case of biased and unbiased knowledge.
Linear Threshold
Kaushik Sarkar | Published Saturday, November 03, 2012 | Last modified Saturday, April 27, 2013NetLogo implementation of Linear Threshold model of influence propagation.
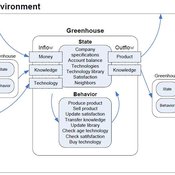
Universal Darwinism in Dutch Greenhouses
Julia Kasmire | Published Wednesday, May 09, 2012 | Last modified Saturday, April 27, 2013An ABM, derived from a case study and a series of surveys with greenhouse growers in the Westland, Netherlands. Experiments using this model showshow that the greenhouse horticulture industry displays diversity, adaptive complexity and an uneven distribution, which all suggest that the industry is an evolving system.
Peer reviewed Swidden Farming Version 2.0
C Michael Barton | Published Wednesday, June 12, 2013 | Last modified Wednesday, September 03, 2014Model of shifting cultivation. All parameters can be controlled by the user or the model can be run in adaptive mode, in which agents innovate and select parameters.
Firm explore-exploit of knowledge
Rosanna Garcia | Published Monday, March 28, 2011 | Last modified Saturday, April 27, 2013The basic premise of the model is to simulate several ‘agents’ going through build-buy cycles: Build: Factories follow simple rules of strategy in the allocation of resources between making exploration and exploitation type products. Buy: Each of two types of Consumers, early-adopters and late adopters, follow simple purchase decision rules in deciding to purchase a product from one of two randomly chosen factories. Thus, the two working ‘agents’ of the model are ‘factories’ and […]
The conditional defector strategy can violate the most crucial supporting mechanisms of cooperation.
Ahmed Ibrahim | Published Tuesday, June 07, 2022Cooperation is essential for all domains of life. Yet, ironically, it is intrinsically vulnerable to exploitation by cheats. Hence, an explanatory necessity spurs many evolutionary biologists to search for mechanisms that could support cooperation. In general, cooperation can emerge and be maintained when cooperators are sufficiently interacting with themselves. This communication provides a kind of assortment and reciprocity. The most crucial and common mechanisms to achieve that task are kin selection, spatial structure, and enforcement (punishment). Here, we used agent-based simulation models to investigate these pivotal mechanisms against conditional defector strategies. We concluded that the latter could easily violate the former and take over the population. This surprising outcome may urge us to rethink the evolution of cooperation, as it illustrates that maintaining cooperation may be more difficult than previously thought. Moreover, empirical applications may support these theoretical findings, such as invading the cooperator population of pathogens by genetically engineered conditional defectors, which could be a potential therapy for many incurable diseases.
Market for Protection
Steven Doubleday | Published Monday, July 01, 2013 | Last modified Monday, August 19, 2013Simulation to replicate and extend an analytical model (Konrad & Skaperdas, 2010) of the provision of security as a collective good. We simulate bandits preying upon peasants in an anarchy condition.
Displaying 10 of 323 results for "John Nay" clear search