About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 425 results for "Therese Lindahl" clear search
Simulating the cost of social care in an ageing population
Eric Silverman | Published Thursday, September 16, 2021This model is an agent-based simulation written in Python 2.7, which simulates the cost of social care in an ageing UK population. The simulation incorporates processes of population change which affect the demand for and supply of social care, including health status, partnership formation, fertility and mortality. Fertility and mortality rates are drawn from UK population data, then projected forward to 2050 using the methods developed by Lee and Carter 1992.
The model demonstrates that rising life expectancy combined with lower birthrates leads to growing social care costs across the population. More surprisingly, the model shows that the oft-proposed intervention of raising the retirement age has limited utility; some reductions in costs are attained initially, but these reductions taper off beyond age 70. Subsequent work has enhanced and extended this model by adding more detail to agent behaviours and familial relationships.
The version of the model provided here produces outputs in a format compatible with the GEM-SA uncertainty quantification software by Kennedy and O’Hagan. This allows sensitivity analyses to be performed using Gaussian Process Emulation.
Agent-Based Model of Social Care with Kinship Networks
Eric Silverman Umberto Gostoli | Published Thursday, October 14, 2021The purpose of this model is the simulation of social care provision in the UK, in which individual agents can decide to provide informal care, or pay for private care, for their loved ones. Agents base these decisions on factors including their own health, employment status, financial resources, relationship to the individual in need and geographical location. The model simulates care provision as a negotiation process conducted between agents across their kinship networks, with agents with stronger familial relationships to the recipient being more likely to attempt to allocate time to care provision. The model also simulates demographic change, the impact of socioeconomic status, and allows agents to relocate and change jobs or reduce working hours in order to provide care.
Despite the relative lack of empirical data in this model, the model is able to reproduce plausible patterns of social care provision. The inclusion of detailed economic and behavioural mechanisms allows this model to serve as a useful policy development tool; complex behavioural interventions can be implemented in simulation and tested on a virtual population before applying them in real-world contexts.
User Guide and Templates for RAT-RS (a reporting standard for improving the documentation of data use in agent-based modelling)
Peer-Olaf Siebers Sebastian Achter Melania Borit Edmund Chattoe-Brown | Published Saturday, March 12, 2022The Rigor and Transparency Reporting Standard (RAT-RS) is a tool to improve the documentation of data use in Agent-Based Modelling. Following the development of reporting standards for models themselves, attention to empirical models has now reached a stage where these standards need to take equally effective account of data use (which until now has tended to be an afterthought to model description). It is particularly important that a standard should allow the reporting of the different uses to which data may be put (specification, calibration and validation), but also that it should be compatible with the integration of different kinds of data (for example statistical, qualitative, ethnographic and experimental) sometimes known as mixed methods research.
For the full details on the RAT-RS, please refer to the related publication “RAT-RS: A Reporting Standard for Improving the Documentation of Data Use in Agent-Based Modelling” (http://dx.doi.org/10.1080/13645579.2022.2049511).
Here we provide supplementary material for this article, consisting of a RAT-RS user guide and RAT-RS templates.
BEEHAVE Extension: Varroa mite control within Good Beekeeping Practice in Germany
Isabel Schödl Jürgen Groeneveld Volker Grimm | Published Wednesday, May 25, 2022 | Last modified Monday, November 07, 2022The western honey bee Apis mellifera is the most important pollinator in the world. The biggest threat to managed honey bees is the ectoparasitic mite Varroa destructor and the viruses DWV (Deformed Wing Virus) and APV (Acute Paralysis Virus) it transmits. Untreated honey bee colonies are expected to die within one to three years. This led to the development of strategies for beekeepers to control the Varroa mite in honey bee colonies and ensure the health and survival of their bee colonies, so called Good Beekeeping Practice. The aim of the extension of BEEHAVE was to represent the Good Beekeeping Practice of Varroa control in Germany. The relevant measures within the Varroa control strategies are drone brood removal as a Varroa trap and the treatment of bee colonies with organic acaricides (formic and oxalic acid) to kill the mites. This extension improves BEEHAVE and builds a bridge between beekeepers in practice and in the modelling world. It vastly contributes to the future use of BEEHAVE in beekeeping education in Germany.
The simulation on the study of the optimal business strategy with the interaction between technologies and consumers.
sej-yoo | Published Monday, June 27, 2022 | Last modified Monday, July 04, 2022HOW IT WORKS
This model consists of three agents, and each agent type operates per business theories as below.
a. New technologies(Tech): It evolves per sustaining or disruptive technology trajectory with the constraint of project management triangle (Scope, Time, Quality, and Cost).
b. Entrepreneurs(Entre): It builds up the solution by combining Tech components per its own strategy (Exploration, Exploitation, or Ambidex).
c. Consumer(Consumer): It selects the solution per its own preference due to Diffusion of innovation theory (Innovators, Early Adopters, Early Majority, Late Majority, Laggards)
…
Peer reviewed Modelling Agricultural Innovations as a Social-Ecological Phenomenon
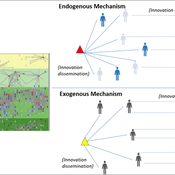
Udita Sanga Maja Schlüter | Published Thursday, November 17, 2022The goal of the AG-Innovation agent-based model is to explore and compare the effects of two alternative mechanisms of innovation development and diffusion (exogenous, linear and endogenous, non-linear) on emergent properties of food and income distribution and adoption rates of different innovations. The model also assesses the range of conditions under which these two alternative mechanisms would be effective in improving food security and income inequality outcomes. Our modelling questions were: i) How do cross-scalar social-ecological interactions within agricultural innovation systems affect system outcomes of food security and income inequality? ii) Do foreign aid-driven exogenous innovation perpetuate income inequality and food insecurity and if so, under which conditions? iii) Do community-driven endogenous innovations improve food security and income inequality and if so, under which conditions? The Ag-Innovation model is intended to serve as a thinking tool for for the development and testing of hypotheses, generating an understanding of the behavior of agricultural innovation systems, and identifying conditions under which alternated innovation mechanisms would improve food security and income inequality outcomes.
An Agent-Based Model of an Insurance Market driven by Supply and Demand with Imperfectly Estimated Strategies in C#
Rei England | Published Sunday, September 24, 2023This is a simulation of an insurance market where the premium moves according to the balance between supply and demand. In this model, insurers set their supply with the aim of maximising their expected utility gain while operating under imperfect information about both customer demand and underlying risk distributions.
There are seven types of insurer strategies. One type follows a rational strategy within the bounds of imperfect information. The other six types also seek to maximise their utility gain, but base their market expectations on a chartist strategy. Under this strategy, market premium is extrapolated from trends based on past insurance prices. This is subdivided according to whether the insurer is trend following or a contrarian (counter-trend), and further depending on whether the trend is estimated from short-term, medium-term, or long-term data.
Customers are modelled as a whole and allocated between insurers according to available supply. Customer demand is calculated according to a logit choice model based on the expected utility gain of purchasing insurance for an average customer versus the expected utility gain of non-purchase.
Evolutionary Model of Subculture Choice
Diogo Alves | Published Monday, December 19, 2022This is an original model of (sub)culture diffusion.
It features a set of agents (dubbed “partygoers”) organized initially in clusters, having properties such as age and a chromosome of opinions about 6 different topics. The partygoers interact with a set of cultures (also having a set of opinions subsuming those of its members), in the sense of refractory or unhappy members of each setting about to find a new culture and trading information encoded in the genetic string (originally encoded as -1, 0, and 1, resp. a negative, neutral, and positive opinion about each of the 6 traits/aspects, e.g. the use of recreational drugs). There are 5 subcultures that both influence (through the aforementioned genetic operations of mutation and recombination of chromosomes simulating exchange of opinions) and are influenced by its members (since a group is a weighted average of the opinions and actions of its constituents). The objective of this feedback loop is to investigate under which conditions certain subculture sizes emerge, but the model is open to many other kinds of explorations as well.
ABM Simulation of Transition from Late Longshan Cultures to Early Erlitou Culture
Carmen Iasiello | Published Sunday, November 26, 2023Within the archeological record for Bronze Age Chinese culture, there continues to be a gap in our understanding of the sudden rise of the Erlitou State from the previous late Longshan chiefdoms. In order to examine this period, I developed and used an agent-based model (ABM) to explore possible socio-politically relevant hypotheses for the gap between the demise of the late Longshan cultures and rise of the first state level society in East Asia. I tested land use strategy making and collective action in response to drought and flooding scenarios, the two plausible environmental hazards at that time. The model results show cases of emergent behavior where an increase in social complexity could have been experienced if a catastrophic event occurred while the population was sufficiently prepared for a different catastrophe, suggesting a plausible lead for future research into determining the life of the time period.
The ABM published here was originally developed in 2016 and its results published in the Proceedings of the 2017 Winter Simulation Conference.
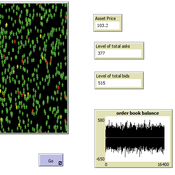
Peer reviewed A financial market with zero intelligence agents
edgarkp | Published Wednesday, March 27, 2024The model’s aim is to represent the price dynamics under very simple market conditions, given the values adopted by the user for the model parameters. We suppose the market of a financial asset contains agents on the hypothesis they have zero-intelligence. In each period, a certain amount of agents are randomly selected to participate to the market. Each of these agents decides, in a equiprobable way, between proposing to make a transaction (talk = 1) or not (talk = 0). Again in an equiprobable way, each participating agent decides to speak on the supply (ask) or the demand side (bid) of the market, and proposes a volume of assets, where this number is drawn randomly from a uniform distribution. The granularity depends on various factors, including market conventions, the type of assets or goods being traded, and regulatory requirements. In some markets, high granularity is essential to capture small price movements accurately, while in others, coarser granularity is sufficient due to the nature of the assets or goods being traded
Displaying 10 of 425 results for "Therese Lindahl" clear search