About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 38 results for "Claude Janin" clear search
Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats
kpadur | Published Friday, September 20, 2024Hybrid attacks coordinate the exploitation of vulnerabilities across domains to undermine trust in authorities and cause social unrest. Whilst such attacks have primarily been seen in active conflict zones, there is growing concern about the potential harm that can be caused by hybrid attacks more generally and a desire to discover how better to identify and react to them. In addressing such threats, it is important to be able to identify and understand an adversary’s behaviour. Game theory is the approach predominantly used in security and defence literature for this purpose. However, the underlying rationality assumption, the equilibrium concept of game theory, as well as the need to make simplifying assumptions can limit its use in the study of emerging threats. To study hybrid threats, we present a novel agent-based model in which, for the first time, agents use reinforcement learning to inform their decisions. This model allows us to investigate the behavioural strategies of threat agents with hybrid attack capabilities as well as their broader impact on the behaviours and opinions of other agents.
DITCH --- A Model of Inter-Ethnic Partnership Formation
Ruth Meyer Laurence Lessard-Phillips Huw Vasey | Published Wednesday, November 05, 2014 | Last modified Tuesday, February 02, 2016The DITCH model has been developed to investigate partner selection processes, focusing on individual preferences, opportunities for contact, and group size to uncover how these may lead to differential rates of inter-ethnic marriage.
TunaFisher ABM
Guus Ten Broeke | Published Wednesday, January 13, 2021TunaFisher ABM simulates the decisions of fishing companies and fishing vessels of the Philippine tuna purse seinery operating in the Celebes and Sulu Seas.
High fishing effort remains in many of the world’s fisheries, including the Philippine tuna purse seinery, despite a variety of policies that have been implemented to reduce it. These policies have predominantly focused on models of cause and effect which ignore the possibility that the intended outcomes are altered by social behavior of autonomous agents at lower scales.
This model is a spatially explicit Agent-based Model (ABM) for the Philippine tuna purse seine fishery, specifically designed to include social behavior and to study its effects on fishing effort, fish stock and industry profit. The model includes economic and social factors of decision making by companies and fishing vessels that have been informed by interviews.
…
Netlogo Earned Value Management Model
Manuel Castañón-Puga Ricardo Fernando Rosales–Cisneros Julio César Acosta–Prado Alfredo Tirado–Ramos Camilo Khatchikian Elías Aburto–Camacllanqui | Published Thursday, November 24, 2022The model aims to illustrate how Earned Value Management (EVM) provides an approach to measure a project’s performance by comparing its actual progress against the planned one, allowing it to evaluate trends to formulate forecasts. The instance performs a project execution and calculates the EVM performance indexes according to a Performance Measurement Baseline (PMB), which integrates the description of the work to do (scope), the deadlines for its execution (schedule), and the calculation of its costs and the resources required for its implementation (cost).
Specifically, we are addressing the following questions: How does the risk of execution delay or advance impact cost and schedule performance? How do the players’ number or individual work capacity impact cost and schedule estimations to finish? Regardless of why workers cause delays or produce overruns in their assignments, does EVM assess delivery performance and help make objective decisions?
To consider our model realistic enough for its purpose, we use the following patterns: The model addresses classic problems of Project Management (PM). It plays the typical task board where workers are assigned to complete a task backlog in project performance. Workers could delay or advance in the task execution, and we calculate the performance using the PMI-recommended Earned Value.
The effect of error on cultural transmission
Claudine Gravel-Miguel | Published Thursday, November 01, 2012 | Last modified Saturday, April 27, 2013This is the replication of the experiment performed by Eerkens and Lipo (2005) to look at the effect of copying errors when specific traits are transferred from an individual to another.
Impact of topography and climate change on Magdalenian social networks
Claudine Gravel-Miguel | Published Monday, September 11, 2017The model presented here was created as part of my dissertation. It aims to study the impacts of topography and climate change on prehistoric networks, with a focus on the Magdalenian, which is dated to between 20 and 14,000 years ago.
Peer reviewed Visibility of archaeological social networks
Claudine Gravel-Miguel | Published Sunday, November 26, 2023The purpose of this model is to explore the impact of combining archaeological palimpsests with different methods of cultural transmission on the visibility of prehistoric social networks. Up until recently, Paleolithic archaeologists have relied on stylistic similarities of artifacts to reconstruct social networks. However, this method - which is successfully applied to more recent ceramic assemblages - may not be applicable to Paleolithic assemblages, as several of those consist of palimpsests of occupations. Therefore, this model was created to study how palimpsests of occupation affect our social network reconstructions.
The model simplifies inter-groups interactions between populations who share cultural traits as they produce artifacts. It creates a proxy archaeological record of artifacts with stylistic traits that can then be used to reconstruct interactions. One can thus use this model to compare the networks reconstructed through stylistic similarities with direct contact.
Armature distribution within the PaleoscapeABM
Claudine Gravel-Miguel | Published Tuesday, March 23, 2021This is a variant of the PaleoscapeABM model available here written by Wren and Janssen. In this variant, we give projectile weapons to hunter and document where they discard them over time. Discard rate and location are influenced by probabilities of hitting/missing the prey, probabilities of damaging the weapon, and probabilities of carrying back embedded projectile armatures to the habitation camp with the body carcass.
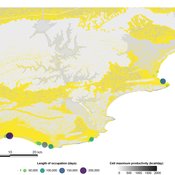
PaleoscapeABM: coastal occupation and shellfish discard
Claudine Gravel-Miguel | Published Tuesday, February 08, 2022This model builds on the Armature distribution within the PaleoscapeABM model, which is itself a variant of the PaleoscapeABM available here written by Wren and Janssen, and.
This model aims to explore where and how much shellfish is discarded at coastal and non-coastal locations by daily coastal foraging. We use this model’s output to test the idea that we can confidently use the archaeological record to evaluate the importance of shellfish in prehistoric people’s diets.
The recognition that aquatic adaptations likely had significant impacts on human evolution triggered an explosion of research on that topic. Recognizing coastal foraging in the past relies on the archaeological signature of that behavior. We use this model to explore why some coastal sites are very intensely occupied and see if it is due to the shellfish productivity of the coast.
Peer reviewed Virus Transmission with Super-spreaders
J Applegate | Published Saturday, September 11, 2021A curious aspect of the Covid-19 pandemic is the clustering of outbreaks. Evidence suggests that 80\% of people who contract the virus are infected by only 19% of infected individuals, and that the majority of infected individuals faile to infect another person. Thus, the dispersion of a contagion, $k$, may be of more use in understanding the spread of Covid-19 than the reproduction number, R0.
The Virus Transmission with Super-spreaders model, written in NetLogo, is an adaptation of the canonical Virus Transmission on a Network model and allows the exploration of various mitigation protocols such as testing and quarantines with both homogenous transmission and heterogenous transmission.
The model consists of a population of individuals arranged in a network, where both population and network degree are tunable. At the start of the simulation, a subset of the population is initially infected. As the model runs, infected individuals will infect neighboring susceptible individuals according to either homogenous or heterogenous transmission, where heterogenous transmission models super-spreaders. In this case, k is described as the percentage of super-spreaders in the population and the differing transmission rates for super-spreaders and non super-spreaders. Infected individuals either recover, at which point they become resistant to infection, or die. Testing regimes cause discovered infected individuals to quarantine for a period of time.
Displaying 10 of 38 results for "Claude Janin" clear search