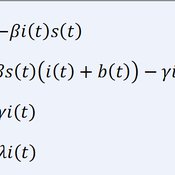About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 494 results for "Jingjing Cai" clear search
Peer reviewed Lethal Geometry
Kristin Crouse | Published Friday, February 21, 2020 | Last modified Wednesday, December 15, 2021LethalGeometry was developed to examine whether territory size influences the mortality risk for individuals within that territory. For animals who live in territoral groups and are lethally aggressive, we can expect that most aggression occurs along the periphery (or border) between two adjacent territories. For territories that are relatively large, the periphery makes up a proportionately small amount of the of the total territory size, suggesting that individuals in these territories might be less likely to die from these territorial skirmishes. LethalGeometry examines this geometric relationship between territory size and mortality risk under realistic assumptions of variable territory size and shape, variable border width, and stochastic interactions and movement.
The individuals (agents) are programmed to walk randomly about their environment, search for and eat food to obtain energy, reproduce if they can, and act aggressively toward individuals of other groups. During each simulation step, individuals analyze their environment and internal state to determine which actions to take. The actions available to individuals include moving, fighting, and giving birth.
Hybrid agent-based methodology for testing response protocols
Fernando Sancho Caparrini | Published Wednesday, February 03, 2021In recent years we have seen multiple incidents with a large number of people injured and killed by one or more armed attackers. Since this type of violence is difficult to predict, detecting threats as early as possible allows to generate early warnings and reduce response time. In this context, any tool to check and compare different action protocols can be a further step in the direction of saving lives. Our proposal combines features from continuous and discrete models to obtain the best of both worlds in order to simulate large and crowded spaces where complex behavior individuals interact. With this proposal we aim to provide a tool for testing different security protocols under several emergency scenarios, where spaces, hazards, and population can be customized. Finally, we use a proof of concept implementation of this model to test specific security protocols under emergency situations for real spaces. Specifically, we test how providing some users of a university college with an app that informs about the type and characteristics of the ongoing hazard, affects in the safety performance.
Agent-Based Model of Social Care with Kinship Networks
Umberto Gostoli Eric Silverman | Published Thursday, October 14, 2021The purpose of this model is the simulation of social care provision in the UK, in which individual agents can decide to provide informal care, or pay for private care, for their loved ones. Agents base these decisions on factors including their own health, employment status, financial resources, relationship to the individual in need and geographical location. The model simulates care provision as a negotiation process conducted between agents across their kinship networks, with agents with stronger familial relationships to the recipient being more likely to attempt to allocate time to care provision. The model also simulates demographic change, the impact of socioeconomic status, and allows agents to relocate and change jobs or reduce working hours in order to provide care.
Despite the relative lack of empirical data in this model, the model is able to reproduce plausible patterns of social care provision. The inclusion of detailed economic and behavioural mechanisms allows this model to serve as a useful policy development tool; complex behavioural interventions can be implemented in simulation and tested on a virtual population before applying them in real-world contexts.
The simulation on the study of the optimal business strategy with the interaction between technologies and consumers.
sej-yoo | Published Monday, June 27, 2022 | Last modified Monday, July 04, 2022HOW IT WORKS
This model consists of three agents, and each agent type operates per business theories as below.
a. New technologies(Tech): It evolves per sustaining or disruptive technology trajectory with the constraint of project management triangle (Scope, Time, Quality, and Cost).
b. Entrepreneurs(Entre): It builds up the solution by combining Tech components per its own strategy (Exploration, Exploitation, or Ambidex).
c. Consumer(Consumer): It selects the solution per its own preference due to Diffusion of innovation theory (Innovators, Early Adopters, Early Majority, Late Majority, Laggards)
…
Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats
kpadur | Published Friday, September 20, 2024Hybrid attacks coordinate the exploitation of vulnerabilities across domains to undermine trust in authorities and cause social unrest. Whilst such attacks have primarily been seen in active conflict zones, there is growing concern about the potential harm that can be caused by hybrid attacks more generally and a desire to discover how better to identify and react to them. In addressing such threats, it is important to be able to identify and understand an adversary’s behaviour. Game theory is the approach predominantly used in security and defence literature for this purpose. However, the underlying rationality assumption, the equilibrium concept of game theory, as well as the need to make simplifying assumptions can limit its use in the study of emerging threats. To study hybrid threats, we present a novel agent-based model in which, for the first time, agents use reinforcement learning to inform their decisions. This model allows us to investigate the behavioural strategies of threat agents with hybrid attack capabilities as well as their broader impact on the behaviours and opinions of other agents.
CITMOD A Tax-Benefit Modeling System for the average citizen
Philip Truscott | Published Monday, August 15, 2011 | Last modified Saturday, April 27, 2013Must tax-benefit policy making be limited to the ‘experts’?
How to not get stuck – an ant model showing how negative feedback due to crowding maintains flexibility in ant foraging
Tomer Czaczkes | Published Thursday, December 17, 2015Positive feedback can lead to “trapping” in local optima. Adding a simple negative feedback effect, based on ant behaviour, prevents this trapping
Product Diffusion Model in an Advance Selling Strategy
Peng Shao | Published Tuesday, March 15, 2016 | Last modified Tuesday, March 15, 2016the model can be used to describe the product diffusion in an Advance Selling Strategy. this model takes into account the consumers product adoption, and describe consumer’s online behavior based on four states.
Modeling Asian-Papuan Admixture during the Neolithic Expansion across Island Southeast Asia
Murray Cox François Vallée | Published Friday, December 09, 2016This Repast Simphony model simulates genomic admixture during the farming expansion of human groups from mainland Asia into the Papuan dominated islands of Southeast Asia during the Neolithic period.
04 TpLab V2.08 – Teleological Pruning Laboratory
Garvin Boyle | Published Saturday, April 15, 2017Our societal belief systems are pruned by evolution, informing our unsustainable economies. This is one of a series of models exploring the dynamics of sustainable economics – PSoup, ModEco, EiLab, OamLab, MppLab, TpLab, CmLab.
Displaying 10 of 494 results for "Jingjing Cai" clear search