About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 263 results for "Ned Wellman" clear search
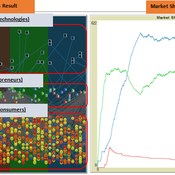
The simulation on the study of the optimal business strategy with the interaction between technologies and consumers.
sej-yoo | Published Monday, June 27, 2022 | Last modified Monday, July 04, 2022HOW IT WORKS
This model consists of three agents, and each agent type operates per business theories as below.
a. New technologies(Tech): It evolves per sustaining or disruptive technology trajectory with the constraint of project management triangle (Scope, Time, Quality, and Cost).
b. Entrepreneurs(Entre): It builds up the solution by combining Tech components per its own strategy (Exploration, Exploitation, or Ambidex).
c. Consumer(Consumer): It selects the solution per its own preference due to Diffusion of innovation theory (Innovators, Early Adopters, Early Majority, Late Majority, Laggards)
…
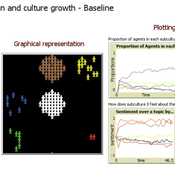
Evolutionary Model of Subculture Choice
Diogo Alves | Published Monday, December 19, 2022This is an original model of (sub)culture diffusion.
It features a set of agents (dubbed “partygoers”) organized initially in clusters, having properties such as age and a chromosome of opinions about 6 different topics. The partygoers interact with a set of cultures (also having a set of opinions subsuming those of its members), in the sense of refractory or unhappy members of each setting about to find a new culture and trading information encoded in the genetic string (originally encoded as -1, 0, and 1, resp. a negative, neutral, and positive opinion about each of the 6 traits/aspects, e.g. the use of recreational drugs). There are 5 subcultures that both influence (through the aforementioned genetic operations of mutation and recombination of chromosomes simulating exchange of opinions) and are influenced by its members (since a group is a weighted average of the opinions and actions of its constituents). The objective of this feedback loop is to investigate under which conditions certain subculture sizes emerge, but the model is open to many other kinds of explorations as well.
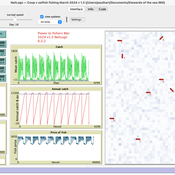
Peer reviewed An IBM of a fishing fleet exploiting a pelagic resource and with a fisher management system. A preliminary version.
Paul Hart | Published Tuesday, March 19, 2024A fisher directed management system was describeded by Hart (2021). It was proposed that fishers should only be allowed to exploit a resource if they collaborated in a resource management system for which they would own and be collectively responsible for. As part of the system fishers would need to follow the rules of exploitation set by the group and provide a central unit with data with which to monitor the fishery. Any fisher not following the rules would at first be fined but eventually expelled from the fishery if he/she continued to act selfishly. This version of the model establishes the dynamics of a fleet of vessels and controls overfishing by imposing fines on fishers whose income is low and who are tempted to keep fishing beyond the set quota which is established each year depending on the abundance of the fish stock. This version will later be elaborated to have interactions between the fishers including pressure to comply with the norms set by the group and which could lead to a stable management system.
Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats
kpadur | Published Friday, September 20, 2024Hybrid attacks coordinate the exploitation of vulnerabilities across domains to undermine trust in authorities and cause social unrest. Whilst such attacks have primarily been seen in active conflict zones, there is growing concern about the potential harm that can be caused by hybrid attacks more generally and a desire to discover how better to identify and react to them. In addressing such threats, it is important to be able to identify and understand an adversary’s behaviour. Game theory is the approach predominantly used in security and defence literature for this purpose. However, the underlying rationality assumption, the equilibrium concept of game theory, as well as the need to make simplifying assumptions can limit its use in the study of emerging threats. To study hybrid threats, we present a novel agent-based model in which, for the first time, agents use reinforcement learning to inform their decisions. This model allows us to investigate the behavioural strategies of threat agents with hybrid attack capabilities as well as their broader impact on the behaviours and opinions of other agents.
Digital divide and opinion formation
Dongwon Lim | Published Friday, November 02, 2012 | Last modified Monday, May 20, 2013This model extends the bounded confidence model of Deffuant and Weisbuch. It introduces online contexts in which a person can deliver his or her opinion to several other persons. There are 2 additional parameters accessibility and connectivity.
An empirical ABM for regional land use/cover change: a Dutch case study
Diego Valbuena | Published Saturday, March 12, 2011 | Last modified Thursday, November 11, 2021This is an empirical model described in http://dx.doi.org/10.1016/j.landurbplan.2010.05.001. The objective of the model is to simulate how the decision-making of farmers/agents with different strategies can affect the landscape structure in a region in the Netherlands.
A simple emulation-based computational model
Carlos Fernández-Márquez Francisco J Vázquez | Published Tuesday, May 21, 2013 | Last modified Tuesday, February 05, 2019Emulation is one of the simplest and most common mechanisms of social interaction. In this paper we introduce a descriptive computational model that attempts to capture the underlying dynamics of social processes led by emulation.
An Agent-Based Model of Collective Action
Hai-Hua Hu | Published Tuesday, August 20, 2013We provide an agent-based model of collective action, informed by Granovetter (1978) and its replication model by Siegel (2009). We use the model to examine the role of ICTs in collective action under different cultural and political contexts.
Societal Simulator v203
Tim Gooding | Published Tuesday, October 01, 2013 | Last modified Friday, November 28, 2014Designed to capture the evolutionary forces of global society.
MCR Model
Davide Secchi Nuno R Barros De Oliveira | Published Friday, July 22, 2016 | Last modified Saturday, January 23, 2021The aim of the model is to define when researcher’s assumptions of dependence or independence of cases in multiple case study research affect the results — hence, the understanding of these cases.
Displaying 10 of 263 results for "Ned Wellman" clear search