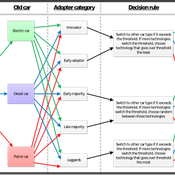
About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 1068 results for "J A Cuesta" clear search
Social and ecological feedback in greening behavior
Athena Aktipis | Published Thursday, February 19, 2015We construct an agent-based model to investigate and understand the roles of green attachment, engagement in local ecological investment (i.e., greening), and social feedback.
(De-)Stabilising effect of diffusions
Julia Kasmire Bert Van Meeuwen Cornelis Eikelboom | Published Tuesday, August 11, 2015What is stable: the large but coordinated change during a diffusion or the small but constant and uncoordinated changes during a dynamic equilibrium? This agent-based model of a diffusion creates output that reveal insights for system stability.
Peer reviewed Industrial Symbiosis Network implementation ABM
Kasper Pieter Hendrik Lange Gijsbert Korevaar Igor Nikolic Paulien Herder | Published Tuesday, December 01, 2020 | Last modified Wednesday, June 16, 2021The purpose of the model is to explore the influence of actor behaviour, combined with environment and business model design, on the survival rates of Industrial Symbiosis Networks (ISN), and the cash flows of the agents. We define an ISN to be robust, when it is able to run for 10 years, without falling apart due to leaving agents.
The model simulates the implementation of local waste exchange collaborations for compost production, through the ISN implementation stages of awareness, planning, negotiation, implementation, and evaluation.
One central firm plays the role of waste processor in a local composting initiative. This firm negotiates with other firms to become a supplier of their organic residual streams. The waste suppliers in the model can decide to join the initiative, or to have the waste brought to the external waste incinerator. The focal point of the model are the company-level interactions during the implementation or ending of synergies.
…
Agent-based tax evasion model for investigating impacts of public disclosure
Hiroyuki Sano | Published Thursday, March 14, 2024The model explores the impact of public disclosure on tax compliance among diverse agents, including individual taxpayers and a tax authority. It incorporates heterogeneous preferences and income endowments among taxpayers, captured through a utility function that considers psychic costs subtracted from expected pecuniary utility. These costs include moral, reciprocity, and stigma costs associated with norm violations, leading to variations in taxpayers’ risk attitudes and related parameters. The tax authority’s attributes, such as the frequency of random audits, penalty rate, and the choice between partial or full disclosure, remain fixed throughout the simulation. Income endowments and preference parameters are randomly assigned to taxpayers at the outset.
Taxpayers maximize their expected utility by reporting income, taking into account tax, penalty, and audit rates. They make annual decisions based on their own and their peers’ behaviors from the previous year. Taxpayers indirectly interact at the societal level through public disclosure conducted by the tax authority, exchanging tax information among peers. Each period in the simulation collects data on total reported income, average compliance rates per income group, distribution of compliance rates, counts of compliers, full evaders, partial evaders, and the numbers of taxpayers experiencing guilt and anger. The model evaluates whether public disclosure positively or negatively impacts compliance rates and quantifies this impact based on aggregated individual reporting behaviors.
Peer reviewed ELTAP-Egy model (Energy Landscape Transition Analysis and Planning in Egypt)
Mostafa Shaaban Jürgen Scheffran Jürgen Böhner Mohamed Salah Elsobki | Published Saturday, December 29, 2018The model investigates conditions, scenarios and strategies for future planning of energy in Egypt, with an emphasis on alternative energy pathways and a sustainable electricity supply mix as part of an energy roadmap till the year 2100. It combines the multi-criteria decision analysis (MCDA) with agent-based modeling (ABM) and Geographic Information Systems (GIS) visualization to integrate the interactions of the decisions of multi-agents, the multi-criteria evaluation of sustainability, the time factor and the site factors to assess the transformation of energy landscapes.
Peer reviewed An agent-based model for brain drain
Furkan Gürsoy Bertan Badur | Published Wednesday, March 03, 2021 | Last modified Friday, March 12, 2021An agent-based model for the emigration of highly-skilled labour.
We hypothesise that there are two main factors that impact the decision and ability to move abroad: desire to maximise individual utility and network effects. Accordingly, several factors play role in brain drain such as the overall economic and social differences between the home and host countries, people’s ability and capacity to obtain good jobs and start a life abroad, the barriers of moving abroad, and people’s social network who are already working abroad.
Simulating changing traffic flow caused by new bus route in Augsburg
Eduard | Published Wednesday, August 04, 2021This is a Netlogo model which simulates car and bus/tram traffic in Augsburg, specifically between the districts Stadtbergen, Göggingen and the Königsplatz. People either use their cars or public transport to travel to one of their random destinations (Stadtbergen or Göggingen), performing some activity and then returning to their home. Attributes such as travel and waiting time as well as their happiness upon arriving are stored and have an impact on individuals on whether they would consider changing their mode of transport or not.
MUGS - Model of Urban Green Spaces
Stefano Picascia | Published Friday, September 17, 2021Abstract model investigating the determinants of inter- and intra-urban inequality in contact with nature. We explore the plausibility of a social integration hypothesis - whereby the primary factor in decisions to visit Urban Green Spaces (UGS) is an assessment of who else is likely to be using the space at the same time, and the assessment runs predominantly along class lines. The model simulates four cities in Scotland and shows the conditions under which the mechanisms theorised are sufficient to reproduce observed inequalities in UGS usage.
Relational Social Interaction Model of Migration (RSIMM)
Sean Bergin Christopher Roberts | Published Monday, February 07, 2011 | Last modified Saturday, April 27, 2013Current trends suggest that when individuals of different cultural backgrounds encounter one another, their social categories become entangled and create new hybridized or creole identities.
Hohokam Water Management Simulation (HWM)
John Murphy | Published Wednesday, August 31, 2011 | Last modified Saturday, April 27, 2013Simulation of irrigation system management using archaeological data from southern Arizona
Displaying 10 of 1068 results for "J A Cuesta" clear search