About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 145 results for "Reginald Lee Hayes" clear search
This model was design to test parameters that affects the number of people shot during mass shooting. This basic formulation places a gunman in a crowd and allows the users to manipulate parameters of the gunman.
On July 20th, James Holmes committed a mass shooting in a midnight showing of The Dark Knight Rises. The Aurora Colorado shooting was used as a test case to validate this framework for modeling mass shootings.
MIXTRUST - crop-livestock interactions at regional level
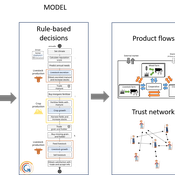
Myriam Grillot Aurélien Peter | Published Tuesday, February 25, 2025The basic idea behind developing MIXTRUST was to represent a network of agricultural stakeholders composed of farmers and a cooperative in a mixed landscape to test its performances in response to risks. A mixed landscape here is a landscape where crop and livestock systems interact by the intermediary of material flows of agricultural products. It can be within mixed farms, or between farms, often specialized, (e.g. straw-manure).
Simulating Water, Individuals, and Management (SWIM)
John Murphy | Published Friday, July 05, 2019SWIM is a simulation of water management, designed to study interactions among water managers and customers in Phoenix and Tucson, Arizona. The simulation can be used to study manager interaction in Phoenix, manager and customer messaging and water conservation in Tucson, and when coupled to the Water Balance Model (U New Hampshire), impacts of management and consumer choices on regional hydrology.
Publications:
Murphy, John T., Jonathan Ozik, Nicholson T. Collier, Mark Altaweel, Richard B. Lammers, Alexander A. Prusevich, Andrew Kliskey, and Lilian Alessa. “Simulating Regional Hydrology and Water Management: An Integrated Agent-Based Approach.” Winter Simulation Conference, Huntington Beach, CA, 2015.
Simulating the cost of social care in an ageing population
Eric Silverman | Published Thursday, September 16, 2021This model is an agent-based simulation written in Python 2.7, which simulates the cost of social care in an ageing UK population. The simulation incorporates processes of population change which affect the demand for and supply of social care, including health status, partnership formation, fertility and mortality. Fertility and mortality rates are drawn from UK population data, then projected forward to 2050 using the methods developed by Lee and Carter 1992.
The model demonstrates that rising life expectancy combined with lower birthrates leads to growing social care costs across the population. More surprisingly, the model shows that the oft-proposed intervention of raising the retirement age has limited utility; some reductions in costs are attained initially, but these reductions taper off beyond age 70. Subsequent work has enhanced and extended this model by adding more detail to agent behaviours and familial relationships.
The version of the model provided here produces outputs in a format compatible with the GEM-SA uncertainty quantification software by Kennedy and O’Hagan. This allows sensitivity analyses to be performed using Gaussian Process Emulation.
The Regional Security Game: An Agent-based, Evolutionary Model of Strategic Evolution and Stability
Anthony Skews | Published Saturday, June 09, 2018The Regional Security Game is a iterated public goods game with punishement based on based on life sciences work by Boyd et al. (2003 ) and Hintze & Adami (2015 ), with modifications appropriate for an international relations setting. The game models a closed regional system in which states compete over the distribution of common security benefits. Drawing on recent work applying cultural evolutionary paradigms in the social sciences, states learn through imitation of successful strategies rather than making instrumentally rational choices. The model includes the option to fit empirical data to the model, with two case studies included: Europe in 1933 on the verge of war and south-east Asia in 2013.
Cultural transmission in structured populations
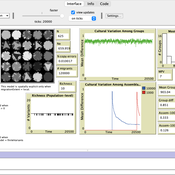
Luke Premo | Published Wednesday, November 13, 2024This structured population model is built to address how migration (or intergroup cultural transmission), copying error, and time-averaging affect regional variation in a single selectively neutral discrete cultural trait under different mechanisms of cultural transmission. The model allows one to quantify cultural differentiation between groups within a structured population (at equilibrium) as well as between regional assemblages of time-averaged archaeological material at two different temporal scales (1,000 and 10,000 ticks). The archaeological assemblages begin to accumulate only after a “burn-in” period of 10,000 ticks. The model includes two different representations of copying error: the infinite variants model of copying error and the finite model of copying error. The model also allows the user to set the variant ceiling value for the trait in the case of the finite model of copying error.
NarrABS
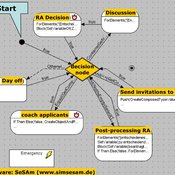
Tilman Schenk | Published Thursday, September 20, 2012 | Last modified Saturday, April 27, 2013An agent based simulation of a political process based on stakeholder narratives
Bicycle model
Dana Kaziyeva Gudrun Wallentin Martin Loidl | Published Thursday, January 10, 2019 | Last modified Monday, February 22, 2021The purpose of the model is to generate the spatio-temporal distribution of bicycle traffic flows at a regional scale level. Disaggregated results are computed for each network segment with the minute time step. The human decision-making is governed by probabilistic rules derived from the mobility survey.
Tram Commute
Julia Kasmire | Published Thursday, February 13, 2020 | Last modified Monday, March 02, 2020A demonstration model showing how modellers can create a multi regional tram network with commuters, destinations and houses. The model offers options to create a random tram network made from modeller input or to load shapefiles for the Greater Manchester Metrolink.
The model uses NetLogo with gis, nw an csv extensions.
Displaying 10 of 145 results for "Reginald Lee Hayes" clear search