About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 24 results for "Claudia Munoz-Zanzi" clear search
Peer reviewed MHMSLeptoDy (Multi-host, multi-serovar Leptospira Dynamics Model)
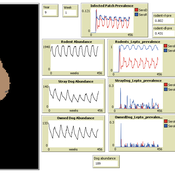
Aniruddha Belsare Meghan Mason Matthew Gompper Claudia Munoz-Zanzi | Published Tuesday, January 29, 2019 | Last modified Tuesday, March 12, 2019Leptospirosis is a neglected, bacterial zoonosis with worldwide distribution, primarily a disease of poverty. More than 200 pathogenic serovars of Leptospira bacteria exist, and a variety of species may act as reservoirs for these serovars. Human infection is the result of direct or indirect contact with Leptospira bacteria in the urine of infected animal hosts, primarily livestock, dogs, and rodents. There is increasing evidence that dogs and dog-adapted serovar Canicola play an important role in the burden of leptospirosis in humans in marginalized urban communities. What is needed is a more thorough understanding of the transmission dynamics of Leptospira in these marginalized urban communities, specifically the relative importance of dogs and rodents in the transmission of Leptospira to humans. This understanding will be vital for identifying meaningful intervention strategies.
One of the main objectives of MHMSLeptoDy is to elucidate transmission dynamics of host-adapted Leptospira strains in multi-host system. The model can also be used to evaluate alternate interventions aimed at reducing human infection risk in small-scale communities like urban slums.
A model of groundwater usage by farmers in the Upper Guadiana, Spain
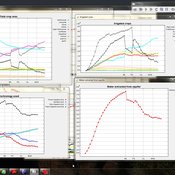
Georg Holtz | Published Thursday, June 30, 2011 | Last modified Saturday, April 27, 2013An agent-based model to investigate the history of irrigated agriculture in the Upper Guadiana Basin, Spain, in order to learn about the influence of farmers’ characteristics (inter alia profit orientation, risk aversion, skills, available labour force and farm size) on land-use change and associated groundwater over-use in this region.
Peer reviewed MADTOR: Model for Assessing Drug Trafficking Organizations Resilience
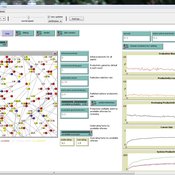
Deborah Manzi | Published Friday, February 23, 2024Criminal organizations operate in complex changing environments. Being flexible and dynamic allows criminal networks not only to exploit new illicit opportunities but also to react to law enforcement attempts at disruption, enhancing the persistence of these networks over time. Most studies investigating network disruption have examined organizational structures before and after the arrests of some actors but have disregarded groups’ adaptation strategies.
MADTOR simulates drug trafficking and dealing activities by organized criminal groups and their reactions to law enforcement attempts at disruption. The simulation relied on information retrieved from a detailed court order against a large-scale Italian drug trafficking organization (DTO) and from the literature.
The results showed that the higher the proportion of members arrested, the greater the challenges for DTOs, with higher rates of disrupted organizations and long-term consequences for surviving DTOs. Second, targeting members performing specific tasks had different impacts on DTO resilience: targeting traffickers resulted in the highest rates of DTO disruption, while targeting actors in charge of more redundant tasks (e.g., retailers) had smaller but significant impacts. Third, the model examined the resistance and resilience of DTOs adopting different strategies in the security/efficiency trade-off. Efficient DTOs were more resilient, outperforming secure DTOs in terms of reactions to a single, equal attempt at disruption. Conversely, secure DTOs were more resistant, displaying higher survival rates than efficient DTOs when considering the differentiated frequency and effectiveness of law enforcement interventions on DTOs having different focuses in the security/efficiency trade-off.
Overall, the model demonstrated that law enforcement interventions are often critical events for DTOs, with high rates of both first intention (i.e., DTOs directly disrupted by the intervention) and second intention (i.e., DTOs terminating their activities due to the unsustainability of the intervention’s short-term consequences) culminating in dismantlement. However, surviving DTOs always displayed a high level of resilience, with effective strategies in place to react to threatening events and to continue drug trafficking and dealing.
Activation Regimes in Opinion Dynamics
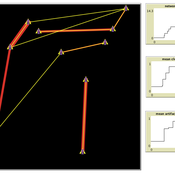
Meysam Alizadeh Claudio Cioffi-Revilla | Published Tuesday, September 01, 2015We compare the effect of four activation regimes by measuring the appropriate opinion clustering statistics and also the number of emergent extremists.
Peer Review Model
Flaminio Squazzoni Claudio Gandelli | Published Wednesday, September 05, 2012 | Last modified Saturday, April 27, 2013This model looks at implications of author/referee interaction for quality and efficiency of peer review. It allows to investigate the importance of various reciprocity motives to ensure cooperation. Peer review is modelled as a process based on knowledge asymmetries and subject to evaluation bias. The model includes various simulation scenarios to test different interaction conditions and author and referee behaviour and various indexes that measure quality and efficiency of evaluation […]
Peer reviewed An agent-based model to identify management practices, integrity and performance in Kenya’s and Ghana’s Water Service Delivery
Francesc Bellaubi Georg Holtz Claudia Pahl-Wostl | Published Sunday, March 09, 2014 | Last modified Tuesday, July 15, 2014The ABM looks at how the performance of Water Service Delivery is affected by the relation between management practices and integrity in terms of transparency, accountability and participation
The effect of error on cultural transmission
Claudine Gravel-Miguel | Published Thursday, November 01, 2012 | Last modified Saturday, April 27, 2013This is the replication of the experiment performed by Eerkens and Lipo (2005) to look at the effect of copying errors when specific traits are transferred from an individual to another.
Impact of topography and climate change on Magdalenian social networks
Claudine Gravel-Miguel | Published Monday, September 11, 2017The model presented here was created as part of my dissertation. It aims to study the impacts of topography and climate change on prehistoric networks, with a focus on the Magdalenian, which is dated to between 20 and 14,000 years ago.
Peer reviewed Visibility of archaeological social networks
Claudine Gravel-Miguel | Published Sunday, November 26, 2023The purpose of this model is to explore the impact of combining archaeological palimpsests with different methods of cultural transmission on the visibility of prehistoric social networks. Up until recently, Paleolithic archaeologists have relied on stylistic similarities of artifacts to reconstruct social networks. However, this method - which is successfully applied to more recent ceramic assemblages - may not be applicable to Paleolithic assemblages, as several of those consist of palimpsests of occupations. Therefore, this model was created to study how palimpsests of occupation affect our social network reconstructions.
The model simplifies inter-groups interactions between populations who share cultural traits as they produce artifacts. It creates a proxy archaeological record of artifacts with stylistic traits that can then be used to reconstruct interactions. One can thus use this model to compare the networks reconstructed through stylistic similarities with direct contact.
Armature distribution within the PaleoscapeABM
Claudine Gravel-Miguel | Published Tuesday, March 23, 2021This is a variant of the PaleoscapeABM model available here written by Wren and Janssen. In this variant, we give projectile weapons to hunter and document where they discard them over time. Discard rate and location are influenced by probabilities of hitting/missing the prey, probabilities of damaging the weapon, and probabilities of carrying back embedded projectile armatures to the habitation camp with the body carcass.
Displaying 10 of 24 results for "Claudia Munoz-Zanzi" clear search